Understanding Incident Response: A Comprehensive Guide
Incident Response is a crucial aspect of cybersecurity management that focuses on preparing for, detecting, and responding to security breaches effectively. Organizations face various cyber threats that can jeopardize sensitive data, disrupt operations, and damage reputation. Therefore, a well-defined Incident Response plan is essential to mitigate risks and manage incidents when they occur.
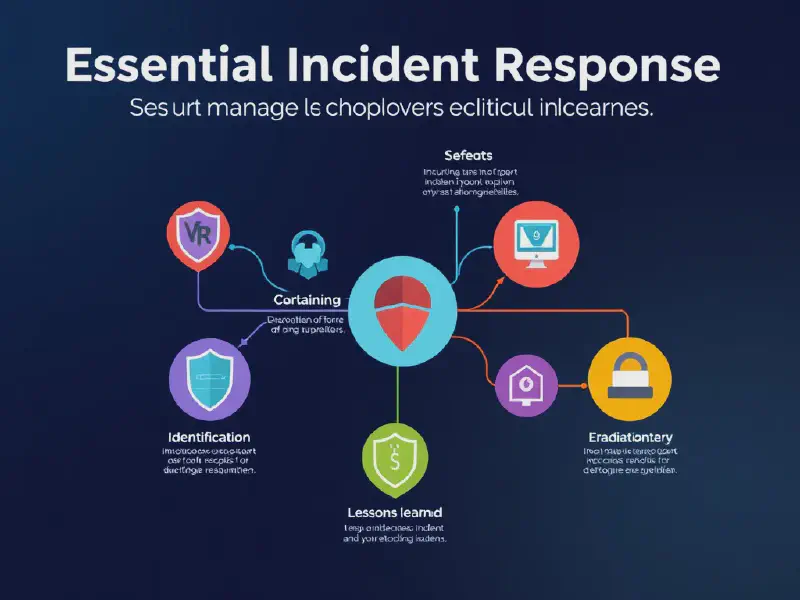
An effective Incident Response process involves several key steps, including preparation, detection and analysis, containment, eradication, recovery, and post-incident review. Each of these phases plays a vital role in ensuring an organization's ability to respond to incidents promptly and minimize potential damage. By understanding and implementing a robust Incident Response strategy, organizations can enhance their security posture and resilience against cyber threats.
Preparation for Incident Response is the first and perhaps the most critical phase. Organizations must develop an Incident Response plan tailored to their unique needs, establish a dedicated Incident Response team, conduct regular training and drills, and define clear roles and responsibilities for team members. By laying a strong foundation during the preparation phase, organizations can better respond to incidents when they arise.
Effective organizations prioritize proactive measures and develop a comprehensive Incident response plan to mitigate potential threats.
Once an incident is identified, the focus shifts to detection and analysis. This phase involves identifying signs of a security breach, utilizing security monitoring tools, analyzing logs and alerts, and conducting forensic analysis to understand the scope and impact of the incident. The effectiveness of this phase greatly influences the subsequent handling of the incident and its potential containment.
Containment strategies are crucial for limiting the damage caused by a security incident. This phase includes immediate containment actions, distinguishing between short-term and long-term containment strategies, isolating affected systems to prevent further compromise, and implementing network segmentation techniques to enhance security. Effective containment strategies can drastically reduce recovery time and costs associated with an incident.
Preparation for Incident Response
Creating an Incident Response Plan is the first step organizations should take in preparing for potential incidents. This plan defines the protocols, roles, responsibilities, and steps to follow in the event of a security incident, ensuring a swift and organized response to minimize impact.
Establishing an Incident Response Team is vital for effective management of cybersecurity incidents. This team is typically made up of individuals with expertise in various fields, including IT, legal, and public relations, who come together to coordinate incident response efforts and ensure a comprehensive approach is applied to each situation.
Training and Drills for Incident Response are essential to ensure team members are well-prepared to handle incidents. Regular training sessions and simulation drills help build familiarity with the Incident Response plan and improve the overall effectiveness of the team during real incidents.
Defining Roles and Responsibilities within the Incident Response Team clarifies the expectations and duties of each member. This ensures that everyone recognizes their role during an incident, facilitating an organized and efficient response.
Detection and Analysis of Incidents
Identifying Signs of a Security Breach involves monitoring for unusual activity or potential indicators of compromise. Quick identification is crucial in reducing the window of vulnerability and minimizing damage during a security incident.
Utilizing Security Monitoring Tools can greatly enhance an organization's capability to detect incidents. These tools provide real-time analysis of security alerts and automate responses to certain types of threats, allowing for a faster reaction to potential breaches.
Analyzing Logs and Alerts is a critical step in understanding the nature and impact of an incident. By reviewing logs from various sources, organizations can piece together the actions taken by attackers, which can inform containment and eradication efforts.
Conducting Forensic Analysis helps investigate the details of an incident to determine how the breach occurred, its impacts, and what data may have been compromised. Forensic analysis is instrumental in refining future Incident Response strategies and improving overall security posture.
Containment Strategies
Immediate Containment Actions involve the swift measures taken to limit the damage caused by a security incident. These actions might include disabling compromised accounts, shutting down affected systems, or blocking malicious traffic to prevent further intrusion.
Short-term vs Long-term Containment strategies must be determined based on the incident's severity. Short-term containment might include quick fixes to stop immediate damage, while long-term containment involves more comprehensive measures to ensure systems are secure before returning to normal operations.
Isolation of Affected Systems helps prevent the spread of an incident within the network. By isolating compromised systems from the rest of the network, organizations can contain the impact of an attack and gather forensic data without risking further damage.
Network Segmentation Techniques can enhance an organization's security posture by limiting access to sensitive systems and data. By segmenting the network, organizations can effectively contain incidents, making it harder for attackers to move laterally within the network after a breach.
Eradication of Threats
Removing Malware and Backdoors must be a priority during the eradication phase. This step involves thoroughly scanning affected systems to eliminate any malicious software and ensuring that attackers do not retain a foothold in the environment.
Patching Vulnerabilities is essential to prevent similar incidents in the future. Once identified, all vulnerabilities used as entry points during an incident should be patched promptly to enhance the security of the environment.
Cleaning Compromised Systems ensures that any traces of an attack are fully removed, restoring systems to their secure state. This may include reinstalling operating systems or restoring applications to a pre-attack state.
Verifying Completeness of Eradication involves checking to ensure that all threats have been mitigated and that security measures are intact. This may require multiple scans and assessments to provide reassurance that the environment is secure before returning to normal operations.
Recovery and Restoration Procedures
Restoring Affected Systems and Data is critical for returning to normal operations after an incident. This process may include restoring data from secure backups and ensuring all systems are fully operational before going back online.
Implementing Secure Backups ensures that data can be recovered quickly in the event of an incident. Regularly updated and securely stored backups form the backbone of an effective recovery strategy, allowing organizations to mitigate damage effectively.
Testing Systems After Recovery is crucial to ensure that all systems are functioning correctly after restoration. This includes running performance checks and verifying security controls are operational to prevent any residual weaknesses.
Monitoring for Residual Issues helps detect any lingering effects from the incident. Ongoing monitoring after recovery can help identify potential security breaches that may not have been evident immediately after the incident.
Post-Incident Review and Improvement
Conducting a Post-Mortem Analysis allows organizations to reflect on the incident thoroughly. By analyzing what happened, how the response was managed, and the effectiveness of the response strategies, organizations can learn valuable lessons for future improvements.
Updating Incident Response Plans is crucial following any incident. Insights gleaned from the incident can lead to adjustments in the Incident Response Plan, ensuring that the organization is better prepared for similar situations in the future.
Training Staff on New Protocols post-incident review is vital to ensure that everyone involved is aware of the changes made in the Incident Response plan or new processes implemented to enhance security.
Reporting to Stakeholders ensures transparency and accountability within the organization. Keeping stakeholders informed about the incident's impact and the organization's response fosters trust and ensures a cooperative effort toward improving security.
